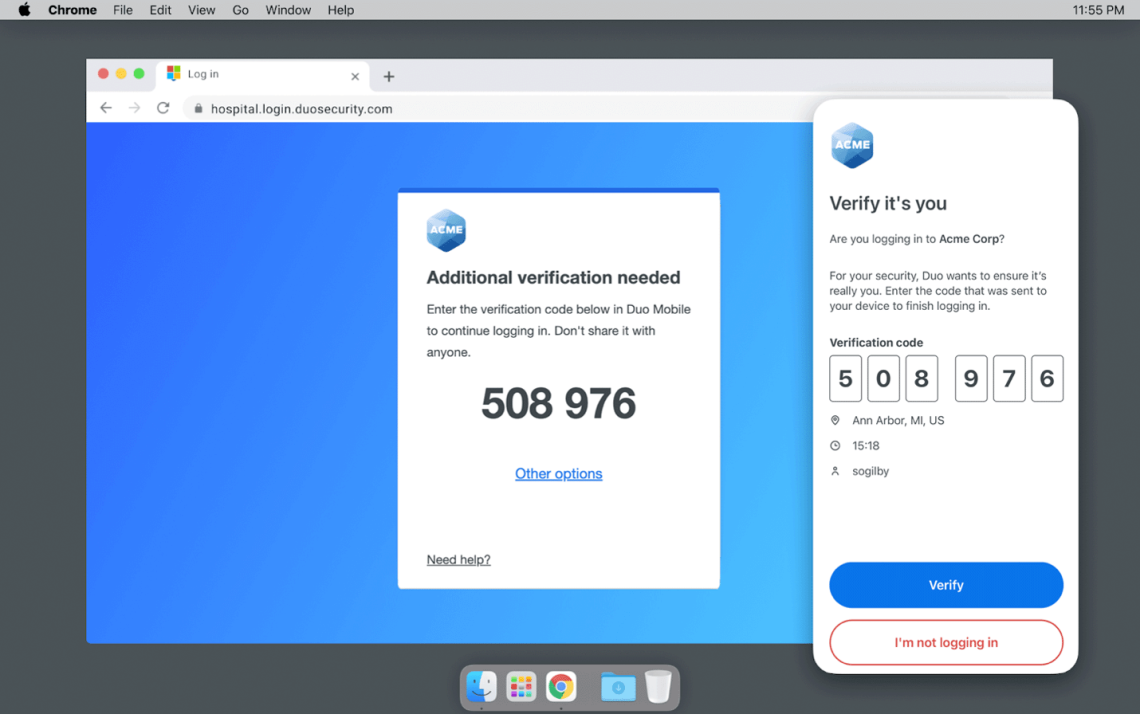
Duo Universal Prompt
This last week has been fun… We are implementing Duo Beyond using Duo Universal Prompt. Multi-Factor Authentication but Duo’s next-gen version. With Universal Prompt we are hoping to cut down on MFA Fatigue by directing users with Macbooks to use Touch ID, users with smartphones to use Duo Mobile and Verified Push, or users who wish to not use the Duo Mobile app, Yubikeys. We are pushing for only FIDO2 MFA methods moving forward.
Custom IDP Factor in Okta
What prompted this fun? Well, we were already in process of rolling out Duo when Uber was popped, in part, due to MFA fatigue and we were tasked with pivoting to only FIDO2 methods moving forward. This required us to rethink many pieces in the process as Duo Universal Prompt is not a small lift. While it’s not in beta with Duo, to support it with Okta we had to enable Custom IDP factor which is an early access feature that came with a few caveats. One is that OIDC would likely not work which meant Jamf Connect would be dead in the water. They also mentioned we could have problems with Okta Workflows after enabling the early access feature. After turning on the feature with Okta support on a Zoom call and determining that none of the caveats affected us we went on out marry way to test.
Testing Microsoft Office for Mac
Testing is where things started to get interesting. We have 15-20 beta testers using Duo Universal Prompt at the moment and we’ve seen a few snags. One is activating Microsoft Office, this might be on how we implemented MFA or how Microsoft defaults to an iFrame when activating Office for Mac. Either way, we have a problem for users who won’t use Duo Mobile. They require a bypass code from the helpdesk but we can’t easily let the user know that this will fail without the bypass code. One plea to Microsoft would be to allow users to activate Office by logging in via a real browser.
Bypass codes are great as a workaround but we are using Device Trust which watches for the latest version of macOS but the iFrame for Microsoft Office activation, or any iFrame, shows up in Duo as macOS 10.15.7 which gets flagged as out of date and doesn’t allow the user to authenticate. So time for a workaround… We use Jamf Pro to manage all our Macs and Jamf knows which machines are on the latest version of macOS as well. We made the decision that if Jamf states the device is up to date then Duo doesn’t need to verify it again. We set up an Okta workflow to trigger when a device is added or removed from our macOS version-compliant smart group. Jamf Pro has Webhook capability that can act in real-time. This calls the API Endpoint action in Okta workflows to first check if the User associated with the device in Jamf is in the Duo macOS version-compliant group and if not we put the user in that group if they were just added to the group in Jamf. I’ll have another post in more detail on this workflow at a later date. The Duo group doesn’t look at the OS version and due to device trust, the user still is limited to using our device to access our data.
Jamf Connect
Duo Universal Prompt and Custom IDP Factor made Jamf Connect rather hampered for us right away. We found that we can use a Custom OIDC Web app instead of the Native Okta integration with Jamf Connect. See the images below for setup. We have the user set up the account and let DEPNotify install Duo Health App (DHA) then ultimately remove the Jamf Connect Login config profile and reset authchanger. We decided that requiring MFA after FileVault was going to be too much of an annoyance to our user base and that Jamf Connect Menu bar app was enough to keep the password in sync.
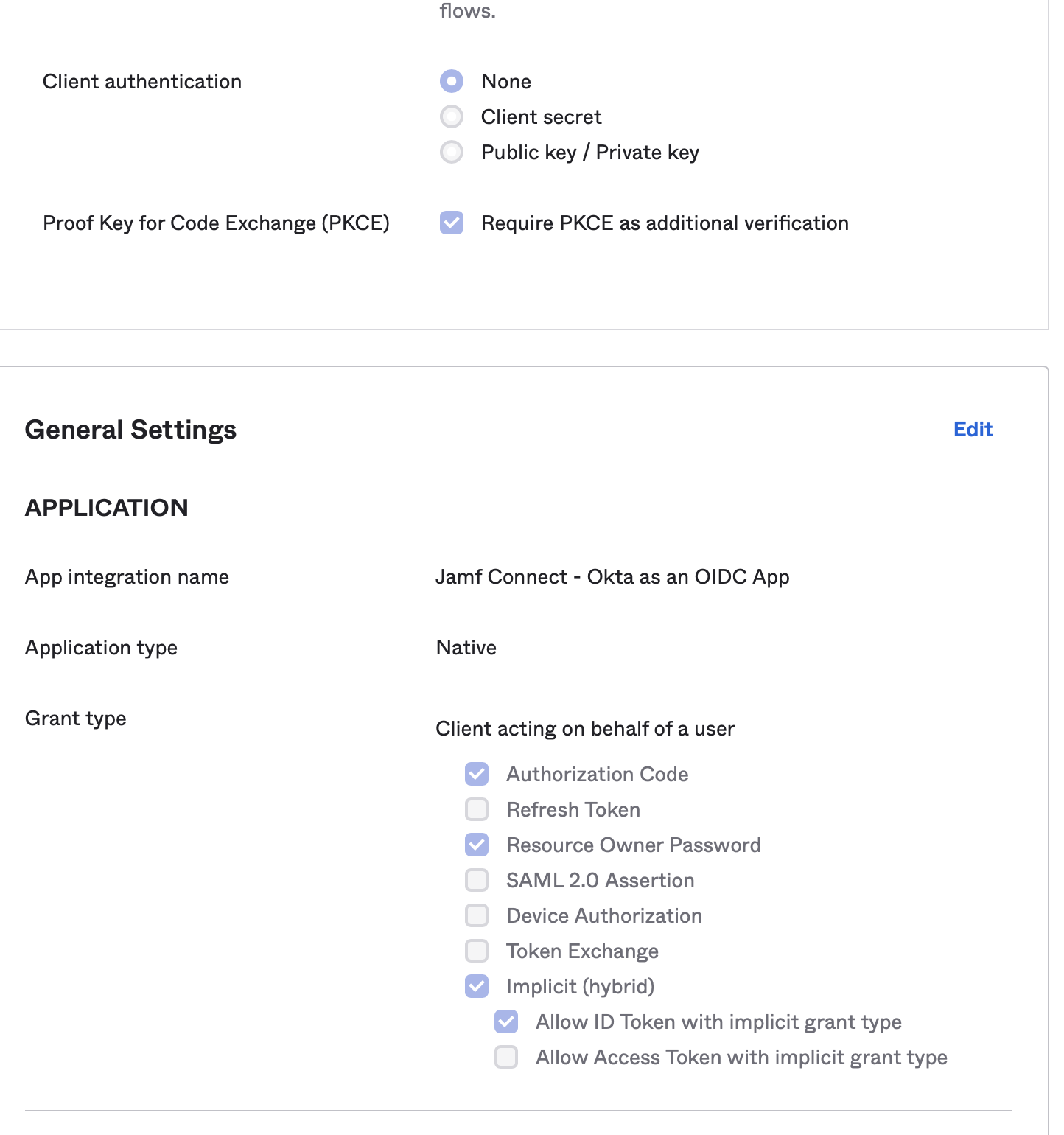
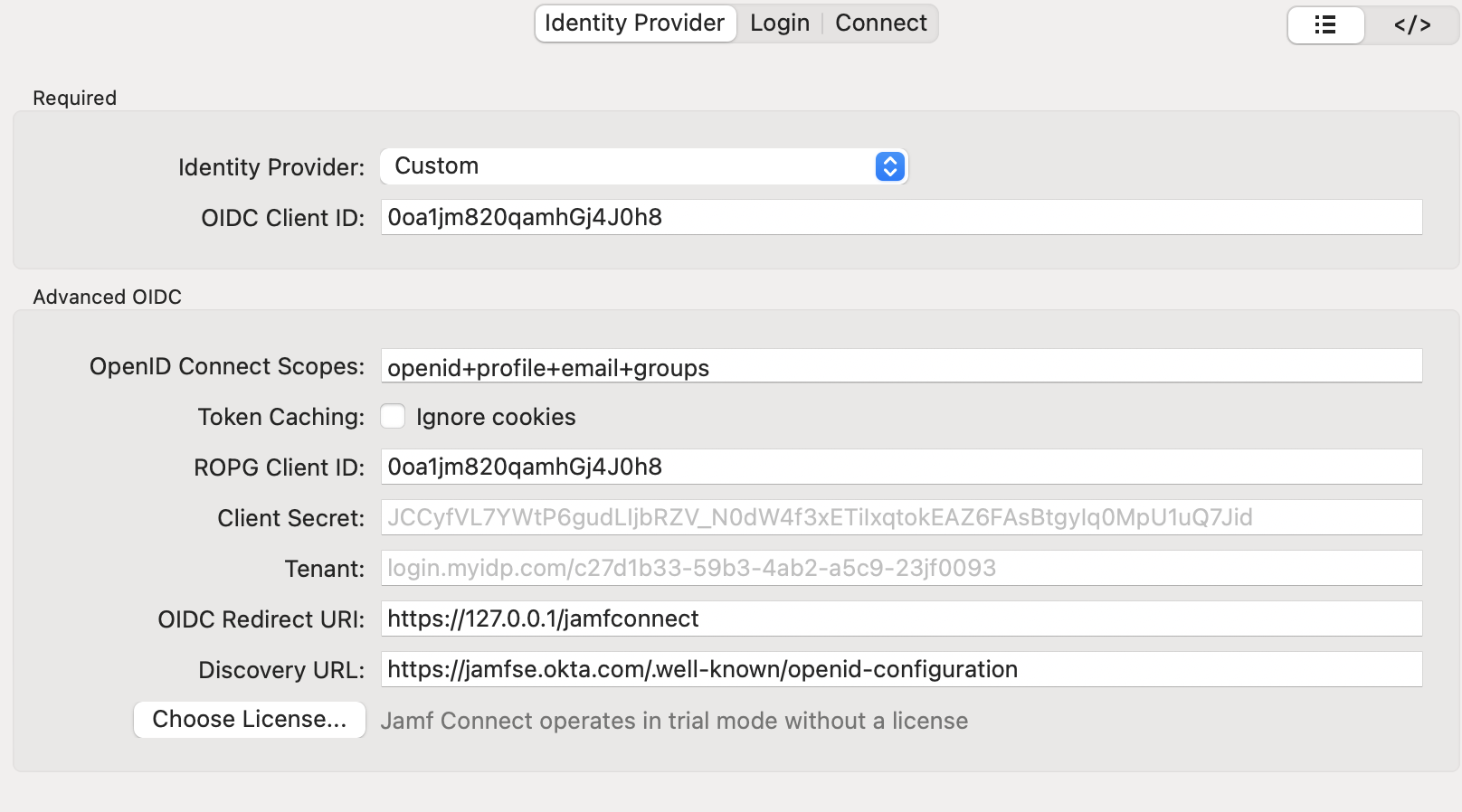
Wrap-up
We believe this will strengthen our security posture and still be a process that our non-technical users and learn and stay secure with. We also have had to automate around Duo as it’s a tool that is rather rigid in its setup. We are thankful for Okta Workflows and the ability to manage Duo and our setup with many Okta workflows.