An Admin’s Guide: How to fix “macOS cannot verify that this app is free from malware”
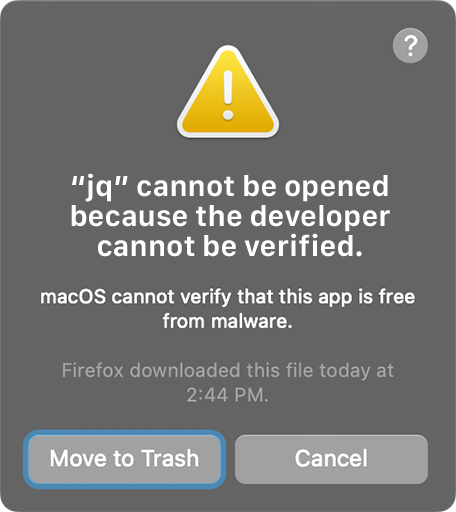
I’ve been building many bash scripts lately that rely on JSON and while there are ways to flip bash to applescript to read said JSON, that just hasn’t worked for me. In stepped JQ which requires me to push this out to my fleet. The only issue I’ve had is that it’s not signed by the developer so GateKeeper will block the use of this app. I know it’s not malware and my end users will never actively use this executable, so how can we bypass Gatekeeper and not have to sign this ourselves?
While doing research to figure out how to get this to work, I found one command that stood out that is something I would never encourage anyone to do, disable gatekeeper entirely. I’m not even gonna put the command in this post just so we don’t have anyone think it’s the fix.
The fix
As many of us do, I packaged up this executable to put in my admin tools folder on each device. Then I added a post install script to run two commands. However, the only command that matters here is the one to the right. This will add the app/executable to the system-wide assessment rule database, basically creating an exception for this tool.
spctl --add "/path/to/app/or/executable"